Quality Assurance Handbook
The Leading Health & Safety and Business Training Provider in the West of Ireland.

Our QA Manual
Please select the section of the Quality Assurance Manual you wish to view.
Section 2 - Governance & Structures for WMC
Section 3 - Documented Approach to QA
Section 4 - Programmes of Education & Training
Section 5 - Staff Recruitment, Management
Section 6 - Teaching and Learning
Section 7 - Assessment of Learners
Section 8 - Support for Learners
Section 9 - Information & Data Management
Section 10 - Public Information & Communication
9.1 Information Management Policy
9.1.1 Purpose
Reliable information and data are available to facilitate informed decision-making at Western Management Centre (WMC). The Centre’s Information Management Policy enables the Centre to securely control and track information and assist the Centre in ensuring compliance with statutory and legal regulations. The WMC Information Management Policy is not a Shared Services Policy.
9.1.2 Policy Statement
This policy outlines WMC’s internal and public information systems used to securely collect, process, and apply information to support the development of successful academic programmes and all related activities.
The WMC Information Management System infrastructure:
- Supports the Centre’s core functions
- Ensures the Centre’s continued compliance with relevant legal and regulatory obligations
- Facilitates accurate reporting to enable specific and prompt decision-making across the Centre’s activities and services
- Indicates commitment to maintaining a robust information security environment
The centre is fully compliant with organisational obligations under data protection legislation and the General Data Protection Regulation (GDPR). The policy applies to all Centre staff, learners, stakeholders, and all Centre records and information, in both hard and soft copy.
9.1.3 Responsibility of
This policy is the responsibility of the Director of Non-Academic Operations.
9.1.4 Processes and Procedures
Learner Management System
WMC maintains learner information using a secure, customised learner management system. Information retained includes learner:
- Personal details
- Contact information
- Assessment results
- Stages completed
- Awards conferred
- Classification of awards
- Certification results
- Personal mitigating circumstances detail
Communications received from learners
The WMC Learning Information System has been customised and configured to meet Centre requirements. This secure and comprehensive database system provides WMC with capabilities to:
- Maintain secure and accurate learner records (for current/historical use)
- Produce reports that contribute to internal quality assurance management and improvement procedures
- Generate data compliance with external regulatory and national systems
Generate statistical and other reports to meet internal and external information requirements
The Centre has arrangements and technical expertise in place to facilitate robust server security systems and the automatic back-up of data in case of technical failure.
Information is maintained securely through protocols of limited access and differing levels of access. Technical support staff, security administrators, system administrators, and others may have need for special account access privileges compared to typical or everyday users. The provision of administrative and special access accounts with a higher level of access means that granting, controlling, managing, and monitoring these accounts is extremely important to WMC’s information security programme.
Management Information Systems
The Centre’s management information system facilitates the storage and retrieval of information as required. The management system enables prompt analysis of key performance indicators and objectives and enable the ongoing monitoring of programmes and all associated services (for more information, see Section 12.1, Internal Review, Monitoring, and Self-Evaluation Policy).
Information Management for Decision-making
The Centre generates reports on learner retention, progression, and completion rates which are used to inform the ongoing monitoring of programmes and all associated services. The Programme Manager is responsible for learner feedback surveys and the generation of associated reports. These reports will feed into the annual monitoring reports for individual programmes. Reports at programme, faculty and institution level are considered to identify influencing factors, determine patterns which assist in benchmarking and inform decision-making, and identify opportunities for additional data analysis that may be of benefit.
Learner achievement reports will be generated by the Programme Manager for consideration by the Results Approval Board (RAP). This information will detail the breakdown of learner performance across individual modules, and final award classification recommendation data will facilitate allowing cross programme analysis and comparative data. A report on analysis will be incorporated into monitoring reports, notified to the External Authenticator, and used to inform programme changes, teaching, learning and assessment strategies or learner support services.
Records Maintenance and Retention
Records retention and management is an important component of the WMC process. The Centre has a need to store and manage information on general operations, student records, and finance as part of day-to-day activities. As part of a retention scheme, classes of documents are retained on different schedules based on various criteria. WMC specific record retention schedules provide a consistent policy regarding retention and disposal of educational and operational records. WMC will set records retention schedules to address legal, statutory, and compliance requirements as well as litigation needs, business processes, and data privacy concerns. Storage requirements shall be coordinated to comply with requirements for record storage.
WMC retention periods are generally determined by:
- Evaluating applicable regulatory, statutory, legal, or general state and federal compliance requirements
- Determining electronic data components collected, their purpose, and applying the appropriate retention procedure to each class of data asset
Identifying other internal or external entities that collect, store, archive, or use WMC information and records
WMC operational areas shall develop procedures and documentation that implement and maintain the retention requirements as outlined in this policy. Specific procedures shall specify the retention time, archival rules, data formats, and the permissible means of storage, access, and encryption (if any).
All staff who create and maintain records as part of their duties are responsible for these records. WMC has arrangements with an external provider to support and maintain backups of all records held in the learner management system.
The Registrar is responsible for the secure storage and maintenance of all assessment documentation and of all transfers of third-party information to other accrediting bodies.
9.2 Privacy Policy
9.2.1 Purpose
Who we are
We are ICE Group. We consist of a number of related companies –ICE Group Business Services, KT Business Skills, ICE Workforce, WMC Galwayand Cokealla (see Figure 13).
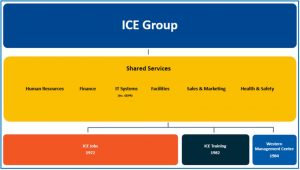
Figure 13–ICE Group Organisational Chart
What we do
Consent
The information we collect and how we use it
Types of people whose data we process
| Recruitment Candidates | Learners /Students /Trainees |
| Clients / Employers / Host Companies | Suppliers |
| Staff | Other People whose data is provided to us by one of the other categories e.g. Referees and Emergency Contacts |
| Agency Workers |
Recruitment Candidate Data and Agency Worker Data
Supplier Data
- If your information has been provided as a Referee by a prospective or actual Recruitment Candidate, Agency Worker, Learner/Student/Trainee, member of Staff, we will use your personal data in order to contact you and obtain a reference. This is part of our quality system and so we deem it to be necessary for our legitimate interests.
- If your information has been provided as an Emergency Contact by a prospective or actual Recruitment Candidate, Agency Worker, Learner/Student/Trainee, or member of Staff, we will use your personal data in order to contact you in the case of an accident or emergency.
This is part of our quality system and so we deem it to be necessary for our legitimate interests.
Learners/Students/Trainees Data
We invite you to provide information to allow us to take steps at your request [or your organisations] prior to providing a training service and to provide the training and associated activities e.g. examination and certification.
This information will normally include your name, address, phone numbers, date of birth, email address and work history, training and education details, and any other information you have chosen to include. It may also include your PPS Number, Course/Programme, Attendance Record, Certification Results, Training Registration Identifier, Training Location, Financial details relating to Allowances or Benefits, as identified by the appropriate Funding, Certification or Awarding organisation or your employer, and CCTV footage if you attend our premises. We will also keep financial details related to your payment’s history. We keep a photo of all Learners/Students/Trainees.
Clients/Employers/Host Companies
To ensure we meet your expectations of our quality service delivery we store your personal data and/or the personal data of individual contacts at your organisation as well as keeping records of our conversations, meetings, communications, transactions and agreements. From time to time, we may also ask you to participate in other activities, which we believe will benefit your organisation or your people. We deem these uses of your data to be necessary for our legitimate interests as an organisation providing our services to you.
Staff
During the hiring process the Recruitment Candidate Data section outlines the data processes. During your employment, we continue to keep the information previously provided and update it as you work with us. We also require you to provide more personal details as required in your position. We will also keep information on your attendance and performance.
Other Data Sources
You may have provided information to other public data sources that we may also process. An example would be where you have posted professional or educational information online, public registers, other service providers etc.
Sharing your information
We will only share your information with as appropriate with
- Our clients, where it is an agreed part of our service
- Prospective employers –to assist them in their hiring processes.
- Individuals and organisations who hold information related to your reference or application to work with us, this includes past employers, educational establishments and examining/awarding bodies, employment agencies.
- Tax, audit or other regulatory authorities that we have a legal obligation to share information with.
- Third party outsourced IT and data management providers where we have appropriate processing agreements or protections in place
- Outsourced service providers, where they are contracted to provide services to us and have agreed to meet our stringent data protection contractual requirements.
- Clients overseas [outside the EU] only where you specifically have expressed an interest in working in another country.
- If we merge with or are acquired by another business, we may share personal information with the new owners of the business and their advisers. You will be sent notice of such an event should it occur.
We may disclose or share your data in order to comply with any legal obligation or in order to enforce or apply our Terms of Business.
Subject Data Access Request
It is important that we have up to date information about you, your career, and educational accomplishments. You have the right to
- Confirm the information we hold
- Modify the information,
- Update it or
- Delete it [ to request delete you must email gdpr@icegroup.ie]
To comply, we will ask you verify your identity, or ask for more information about your request. In some circumstances where we are legally permitted to do so we may decline your request and we will explain why.
Please note that we will not provide the following types of information in response to a data access request: Information about other people; Opinions given in confidence; Repeat requests or privileged information. Other types of information may also be exempt under data protection laws (e.g. data relating to the commission of offences or estimates of damages).
Opt Out
If you no longer wish to be registered with us, you can let us know at any time. Send an email to gdpr@icegroup.ieand we will remove your details.
Job Alerts and Relevant News
We endeavour to keep in touch with you via email and social media. We will send you ‘career and job information’. This will be in the format of ‘job alerts’, ‘career events’ and ‘career and training information’. If you decide that you do not want to receive these please email nomorenews@icegroup.ie or click unsubscribe link on information we sent.
I hereby express my consent to the company to process my personal data for the purposes outlined in the privacy policy.
| Signature | Date |
Statement for CV upload on icejobs.ie
Who we are
We are ICE Group. We consist of a number of related companies –ICE Group Business Services, KT Business Skills, ICE Workforce, WMC Galway and Cokealla.
What we do
We offer varied and flexible recruitment and HR services to clients. We also provide and manage vocational training services for the clients [corporate, public and individual].
Consent
By providing us with your CV you are indicating your consent for ICE Group to process your personal details in the following manner:
The information we collect and how we use it
We invite you to share personal information with us by uploading it through our websites for example through the “Upload your CV” pages.
This information [CV] will normally include your name, address, phone numbers, email address and work history, training and education details, and any other information you have chosen to include.
We use this information to provide our recruitment services, answer your enquiry and provide supplementary services.
We will use your information to match you with jobs we or clients may have. During our recruitment processes we may seek further personal information as appropriate including –proof of identity, educational certification and/or permission to contact your education provider to confirm educational achievements, proof of permission to work in the jurisdiction, your current or past remuneration, pension and benefit details, extra information you choose to tell us, extra information that our Clients may tell us about you, aptitude and skill testing information, physical and mental health information, your IP address, the dates times and frequency with which you access our services and CCTV footage if you attend our premises, or a web based interview. This list is non-exhaustive. We may also invite you to undertake some testing.
We will send some of your personal information to the client.
We will also ask you to provide personal details on other people –your referees, so get their permission, inform them that we will contact them. We require Referees contact details –their name, job title, organisation, work email, phone number so that we can contact them to ask for information they already have about you.
Other Data sources
Other information we may collect and how we use it
Sharing your information
- Prospective employers –to assist them in their hiring processes.
- Individuals and organisations (which may be international) who hold information related to your reference or application to work with us, this includes past employers, educational establishments and examining/awarding bodies, and employment agencies.
- Tax, audit or other regulatory authorities that we have a legal obligation to share information with.
- Third party outsourced IT and data management providers where we have appropriate processing agreements or protections in place
- Outsourced service providers, where they are contracted to provide services to us and have agreed to meet our stringent data protection contractual requirements.
- Clients overseas [outside the EU] only where you specifically have expressed an interest in working in another country.
- If we merge with or are acquired by another business, we may share personal information with the new owners of the business and their advisers. You will be sent notice of such an event should it occur.
Job Alerts and Relevant News
We endeavour to keep in touch with you via email and social media. We will send you ‘career and job’ information. This will be in the format of ‘job alerts’, ‘career events’ and ‘career and training information’.If you decide that you do not want to receive these please email nomorenews@icegroup.ie or click the unsubscribe link on the information we sent.
I hereby express my consent to the company to process my personal data for the purposes outlined in the privacy policy.
| Signature | Date |
Subject Data Access Request
- Confirm the information we hold
- Modify the information,
- Update it or
- Deleteit [to request delete you must email gdpr@icegroup.ie]
To comply, we will ask you verify your identity, or ask for more information about your request. In some circumstances where we are legally permitted to do so we may decline your request and we will explain why.
Please note that we will not provide the following types of information in response to a data access request: Information about other people; Opinions given in confidence; Repeat requests or privileged information. Other types of information may also be exempt under data protection laws (e.g. data relating to the commission of offences or estimates of damages).
Opt Out
If you no longer wish to be registered with us, you can let us know at any time. Send an email to gdpr@icegroup.ie and we will remove your details.
9.3 Data Subject Erasure Request Policy
9.3.1 Purpose
Scope
Responsibilities and Definitions
Procedure
Documentation
- Records of communications relating to a subject access request (Retained for 5 years)
- Records of communications resulting in an action to cease processing personal data (Retained for 5 years)
Appendices
- Provides all the information they require to locate the information the person wants;
- Provides sufficient information to verify the data subject’s identity.
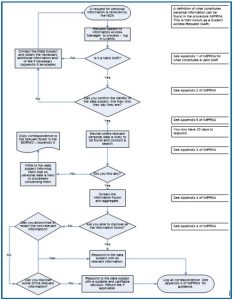
It is unlikely that the first contact from the data subject will provide all the relevant information, in which case the Information Security Manager must write to the data subject requesting this.
Once the Information Security Manager has received all the information they need and sufficient information to verify the data subject’s identity, they have one month to provide the information requested.
Appendix 2 How to correctly identify a Data Subject
Before disclosing any personal information, the Information Security Manager must verify the identity of the data subject.
Whilst it is important that ICE GROUP does not send copies of personal information to people who are not the data subject, they must not appear obstructive. The DPA requires ICE GROUP to take “reasonable measures” to verify the identity of a data subject. The Information Security Manager should keep a record of what measures they take.
If the evidence is insufficient and requires further verification of the data subject’s identity, there are 2 options:
- Telephone the individual and based on the information held about them ask two questions so as to confirm their identity.
- Write to the individual and ask them to send the Information Security Manager a certified copy of their passport, driving licence or birth certificate (this option will take longer and it is also possible that the individual does not have a passport or drivers licence).
Appendix 3 Where to look for personal information
Based on their knowledge of the business area, the Information Security Manager should decide where ‘personal data’ about the individual concerned might be held and locate that information. They may need to search central filing systems electronic and manual, personnel records, shared drives, the Intranet, and/or private filing systems of particular individuals. If necessary, they must also ask colleagues to search their personal drives and e–mail accounts.
If staff are aware of other business areas that might also hold information about the person concerned, please tell the Information Security Manager as soon as possible so that they can arrange for these areas to be searched.
Appendix 4 Howto screen information & what can and cannot be disclosed as a result of a DSAR
Once the Information Security Manager has collected together the information, we hold about a data subject they must examine it in detail to establish if it should be disclosed. This must be done on a case-by-case basis for each individual piece of information. In some cases, they might have to disclose only parts of particular documents.
- Check that the record is actually about the person concerned and not about someone else with the same name. Just because a record contains somebody’s names does not always mean that it is about them. For example, an e-mail might carry the subject line “Meeting about John Smith” but if the e-mail only contains details about whether people can attend the meeting the e-mail is not about John Smith. The Information Security Manager should only print out records/documents/e-mails which are about the person making the subject access request.
- Screen out any duplicate records. For example, if there has been an e-mail exchange with some colleagues, the Information Security Manager only needs to print out the last e-mail in the exchange if copies of all the other e-mails are part of the last e-mail.
- If a record was created by a member of staff acting in a private rather than an official capacity, only exceptional circumstances would justify its disclosure without their consent.If they are not prepared to disclose the record, do not disclose it. Please note however that ICE Group’s IT policies do not permit personal use of the computing facilities.
- The Information Security Manager should only disclose information which is about the person making the subject access request. Where a document contains personal data about a number of individuals, including the data subject, they should not disclose the information about the third parties to the data subject. If the record is primarily about the data subject, with incidental information about others, they should redact the third-partyinformation.If the record is primarily about third parties withhold it if redacting is not possible. Alternatively, contact the third party to obtain consent to disclose the document if possible. Ensure that all correspondence in these matters is logged in the relevant folder in the ICT storage system (see appendix 5).
- The records may contain correspondence and comments about the data subject from a number of parties, including private individuals, external individuals acting in an official capacity, and ICE Group staff. In these cases, we are required to balance the interests of the third party against the interests of the data subject and often omit or redact third party information.
- Do not disclose information which would prejudice the prevention or detection of a crime. For example, if the Gardaí informed us that a member of staff is under investigation, but the member of staff did not know this, then we should not provide that information to the member of staff whilst the investigation is in progress. However, if the investigation is closed or if the member of staff has been informed that there is an investigation underway, then the information should be disclosed in response to a subject access request.
- We should not disclose any records which contain advice from our lawyers, where we are asking for legal advice or which were written as part of obtaining legal advice.
Do not disclose information which is being used, or may be used in future, in negotiations with the data subject if the information gives away our negotiating position and disclosing the information would weaken that negotiating position.
The exemptions identified above are those most likely to apply to information held by the ICE GROUP. There are others and it is good working practice to research all Data Protection Act exemptions before responding to a DSAR (see ICO website for up to date information regarding exemptions).
As the Information Security Manager puts the information together, they may discover material which does not reflect favourably on us. For example, they may find documents which show that standard procedures have not been followed, or documents which may cause offence to the data subject. These documents must be disclosed. However, the Information Security Manager should bring their contents to the attention of the relevant manager and ensure that appropriate action is taken to address any issues they raise.
Staff must not destroy or refuse to disclose records. This is a criminal offence if it is done after you know a subject access request has been made.
Once the Information Security Manager has identified all the information that can be sent in response to a DSAR, one final review of this information as a collection must be made. This is to offset the risks often discovered by aggregating information. For example, the Information Security Manager may have identified that all the information they intend to release is unrestricted in its nature. However, once aggregated there is an inherent risk that additional information could be disclosed or at least interpreted. This must be taken into consideration before the final response is made.
Appendix 5 How to log the requests and responses
The Information Security Manager should logSubject Access Requests in the ICT storage system using the request for information log spreadsheet. Complete the information requested into the spreadsheet and allocate the next available unique reference number to the DSAR from the spreadsheet. This number should be used in all correspondence.
Create a folder for each DSAR –the filename should be made up from the reference number and surname of the applicant e.g. DSR001 –Smith. Each DSAR file should include the following;
- Copies of the correspondence between the Information Security Manager and the data subject and between the Information Security Manager and any other parties.
- A record of any telephone conversation used to verify the identity of the data subject.
- A record of the Information Security Manager’s decisions and how theycame to those decisions.
- Copies of the information sent to the data subject, for example if the information was anonymised keep a copy of the anonymisedor redacted version that was sent.
The folder should be kept for 5 years and then securely destroyed within ICE Group’s records management programme.
Appendix 6 Subject Access Request Template
I understand that you wish to exercise your rights under the Data Protection Act 2018 to:
[Please set out which right you are exercising]
ICE Group are obliged under the Data Protection Act 2018 to satisfy ourselves as to the identity of the person making the request. Accordingly, we require you to provide suitable proof of your identity, such as your original passport or a copy certified by a solicitor of your original passport, plus original utility bills from at least two service providers to your home address.
Also, in order to assist the ICE Group to locate the information which you are seeking in a timely and efficient manner, you should provide as much information as possible as to the type of data which you are seeking, the period during which the data has been held, the persons or departments who are likely to be holding this data and the sites and/or specific locations where such persons or departments are based.
Please send the completed form and any necessary evidence (as appropriate) to the Information Security Manager, ICE Group. We will endeavour to respond to your request as soon as reasonably practicable.
Regards,
Information Security Manager
Policy Compliance
Compliance Measurement
The ICT Dept. and/or Management will verify compliance to this policy through various methods, including but not limited to, periodic walk-throughs, video monitoring, business tool reports, internal and external audits, and feedback to the policy owner.
Exceptions
Any exception to the policy must be approved by the ICT Dept. and/or Management in advance.
Non-Compliance
An employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment.
9.4 Data Breach Policy
9.4.1 Purpose
Please note that General Data Protection Regulation (GDPR) is a Shared Service provided to Western Management Centre (WMC) by its parent company ICE Group.
All of the departments/companies within ICE Group can use these Shared Services as required. The main benefit of Shared Services relates to cost and efficiency management. From an operational perspective, the use of Shared Services avoids duplication and also can avoid potential different outcomes occurring.
Recital 37 of the EU General Data Protection Regulation 2016/679 states that a ‘group of undertakings should cover a controlling undertaking and its controlled undertakings, whereby the controlling undertaking should be the undertaking which can exert a dominant influence over the other undertakings by virtue, for example, of ownership, financial participation or the rules which govern it or the power to have personal data protection rules implemented. An undertaking which controls the processing of personal data in undertakings affiliated to it should be regarded, together with those undertakings, as a group of undertakings.’
ICE Group must have a robust and systematic process for responding to reported data security Incidents and Breaches. This policy is designed to standardize the ICE Group-wide response to any reported Breach or Incident and ensure that they are appropriately logged and managed in accordance with best practice guidelines. Standardised processes and procedures help to ensure ICE Group can act responsibly, respond effectively, and protect its information assets to the extent possible.
Overview
Data breaches are increasingly common occurrences whether caused through human error or malicious intent. ICE Group operations rely on the proper use of Confidential Information and Personally Identifiable Information (PII) on a daily basis. Managing risk and responding in an organized way to Incidents and Breaches is key to operations and required by Colorado state law.
Scope
This policy applies to all ICE Group staff.
Policy
General Information
A ‘Data Security Incident’ or ‘Incident’ shall mean an accidental or deliberate event that results in or constitutes an imminent threat of the unauthorized access, loss, disclosure, modification, disruption, or destruction of communication or information resources of ICE Group.
Common examples of Data Security Incidents include, but are not limited to, any of the following:
- Successful attempts to gain unauthorized access to an ICE Group system or Student or Educator PII regardless of where such information is located
- Unwanted disruption or denial of service
- The unauthorized use of an ICE Group system for the processing or storage of Confidential Information or PII
- Changes to ICE Group system hardware, firmware, or software characteristics without ICE Group’s knowledge, instruction, or consent
- Loss or theft of equipment where Confidential Information or PII is stored
- Unforeseen circumstances such as a fire or flood that could lead to the loss or misuse of Confidential Information or PII
- Human error involving the loss or mistaken transmission of Confidential Information or PII
- Hacking, social engineering, phishing, or other subversive attacks where information is obtained by deceitful practice
A “Data Security Breach” or “Breach” is any Incident where ICE Group cannot put in place controls or take action to reasonably prevent the misuse of Confidential Information or PII. A Breach is also an Incident where data has been misused.
Adopting a standardized and consistent approach to Incident management shall ensure that:
- Incidents are reported in a timely manner and can be properly investigated
- Incidents are handled by appropriately authorized and skilled personnel
- Appropriate levels of management are involved in response management
- Incidents are recorded and documented
- Organisational impacts are understood, and action is taken to prevent further damage
- Evidence is gathered, recorded, and maintained in a form that will withstand internal and external scrutiny
- External agencies, customers, and data users are informed as required
- Incidents are dealt with in a timely manner and normal operations are restored
- Incidents are reviewed to identify improvements in policies and procedures
Incidents can occur locally, in the cloud, or through third party service providers. Reporting and management of Incidents shall occur similarly. Third party providers shall also be governed by contract terms and liability as defined in their operational agreements.
Any contract breach that results in the misuse or unauthorized access to PII by a Service Contract Provider must be handled according to the General Data Protection Regulations.
Data Classifications
Incidents vary in impact and risk depending on a number of mitigating factors including the content and quantity of the data involved. It is critically important that ICE Group management respond quickly and identify the data classification of the Incident. This allows staff to respond accordingly in a timely and thorough manner.
All reported Incidents shall be classified as below in order to assess risk and approaches to mitigate the situation. Data classification shall refer to the following ICE Group data categories:
Public Data – Information intended for public and community use or information that can be made public without any negative impact on ICE Group or its customers. Student PII shall never be considered public data unless the data is Directory Information as defined by ICE Group policy.
Confidential/Internal Data – Information of a more sensitive nature to the business and educational operations of ICE Group. This data represents basic intellectual capital, applications, and general knowledge. Access shall be limited to only those people that need to know as part of their role within ICE Group. Employee and Educator PII (with the exception of PPSNs, financial information, or other critical information) falls within this classification.
Restricted/Highly Confidential Data- Information that, if breached, causes significant damage to ICE Group operations, reputation, and/or business continuity. Access to this information should be highly restricted. Student PII falls into this category of data. Employee or Educator Financial Information, Social Security Numbers, and other critical information also fall into this classification.
Incident Reporting (Incl. GDPR Report)
The following process shall be followed when responding to a suspected Incident:
- Reporting and the ensuing investigation must be prioritized.
- Confirmed or suspected Incidents shall be reported promptly to the Management. A formal report shall be filed that includes full and accurate details of the Incident including who is reporting the Incident and what classification of data is involved.
- Once an Incident is reported, the Information Security Team shall conduct an assessment to establish the severity of the Incident, next steps in response, and potential remedies and solutions. Based on this assessment, the Information Security Team shall determine if this Incident remains an Incident or if it needs to be categorized as a Breach.
- All Incidents and Breaches will be centrally logged and documented to ensure appropriate documentation, oversight, and consistency in response, management, and reporting.
- All Data Breaches relating to PII must be reported to the Data Protection Commission within 72 hours of the Breach being discovered. When reporting a Breach, the GDPR says you must provide:
a) a description of the nature of the personal data breach including, where possible:
b) the categories and approximate number of individuals concerned; and
c) the categories and approximate number of personal data records concerned;
d) the name and contact details of the data protection officer (if your organisation has one) or other contact point where more information can be obtained;
e) a description of the likely consequences of the personal data breach; and
f) a description of the measures taken, or proposed to be taken, to deal with the personal data breach, including, where appropriate, the measures taken to mitigate any possible adverse effects.
g) The ICT team have a template report.
If a breach is likely to result in a high risk to the rights and freedoms of individuals, those concerned must be informed without undue delay
a) Describe the nature of the personal data breach and, at least:
b) the name and contact details for a point of contact where more information can be obtained;
c) a description of the likely consequences of the personal data breach; and a description of the measures taken, or proposed to be taken, to deal with the personal data breach and including, where appropriate, of the measures taken to mitigate any possible adverse effects.
- The GDPR recognises that it will not always be possible to investigate a breach fully within 72 hours to understand exactly what has happened and what needs to be done to mitigate it. Article 33(4) allows you to provide the required information in phases, as long as this is done without undue further delay.
- If ICE Group is acting as a data processor, the requirements on breach reporting should be detailed in the contract between ICE Group and the Data Controller, and vice versa (required under Article 28).
Classification
Data Breaches or Incidents shall be classified as follows:
Critical/Major Breach or Incident – Incidents or Breaches in this category deal with Confidential Information or PII and are on a large scale (ICE Group-wide). All Incidents or Breaches involving Student PII will be classified as Critical or Major. They typically have the following attributes:
- Any Incident that has been determined to be a Breach
Significant Confidential Information or PII loss, potential for lack of business continuity, ICE Group exposure, or irreversible consequences are imminent - Negative media coverage is likely, and exposure is high
Legal or contractual remedies may be required - Requires significant reporting beyond normal operating procedures
- Any breach of contract that involves the misuse or unauthorized access to PII by a Service Contract Provider
Moderately Critical/Serious Incident – Breaches or Incidents in this category typically deal with Confidential Information and are on a medium scale (e.g. <100 users on the internal network, application or database related, limited exposure). Incidents in this category typically have the following attributes:
- Risk to the ICE Group is moderate
- Third party service provider and subcontractors may be involved
- Data loss is possible but localized/compartmentalized, potential for limited business continuity losses, and minimized ICE Group exposure
- Significant user inconvenience is likely
- Service outages are likely while the breach is addressed
- Negative media coverage is possible but exposure is limited
- Disclosure of Educator or Employee PII is contained and manageable
Low Criticality/Minor Incident – Incidents in this category typically deal with personal or internal data and are on a small or individualized scale (e.g. <10 users on the internal network, personal or mobile device related). Incidents in this category typically have the following attributes:
- Risk to the ICE Group is low
- User inconvenience is likely but not ICE Group damaging
- Internal data released but data is not student, employee, or confidential in nature
- Loss of data is totally contained on encrypted hardware
- Incident can be addressed through normal support channels
Incident Response
Management response to any reported Incident shall involve the following activities:
Assess, Contain and Recover Data
All security Incidents shall have immediate analysis of the Incident and an Incident report completed by the Information Security Team or their designee. This analysis shall include a determination of whether this Incident should be characterized as a Breach. This analysis shall be documented and shared with the HR Manager, the affected parties, and any other relevant stakeholders. At a minimum, the Information Security Team shall:
| Steps | Action | Notes |
| A | Containment and Recovery: | Contain the breach, limit further organizational damage, and seek to recover/restore data. |
| 1 | Breach Determination | Determine if the Incident needs to be classified as a Breach.2 |
| 2 | Ascertain the severity of the incident or Breach and determine the level of data involved | See incident Classification |
| 3 | Investigate the Breach or Incident and forward a copy of the Incident report to the Information Security Team | Ensure investigator has appropriate resources including sufficient time and authority. If PII or confidential data has been breached, also contact the Management. In the event that the Incident or Breach is severe, ICE Group Executive Management, General Counsel and the Information Security Team shall be contacted. |
| 4 | Identify the cause of the Incident or breach and whether the situation has been contained. Ensure that any possibility of further data loss is removed or mitigated as far as possible. If this loss cannot be mitigated, any Incident will be characterized as a Breach. | Compartmentalize and eliminate exposure. Establish what steps can or need to be taken to contain the threat from further data loss. Contact all relevant departments who may be able to assist in this process. This may involve actions such as taking systems offline or restricting access to systems to a very small number of staff until more is known about the Incident. |
| 5 | Determine depth and breadth of losses and limit exposure/damages | Can data be physically recovered if damaged through use of backups, restoration or other means? |
| 6 | Notify authorities as appropriate | For criminal activities where property was stolen or fraudulent activity occurred, contact the appropriate authorities and general counsel. Should the Breach involve Student PII that involves a Service Contract Provider, notify the ICE Group Board members. |
| 7 | Ensure all actions and decisions are logged and recorded as part of incident documentation and reporting. | Complete Incident Report and file with Management |
Assess Risk and Incident Scope
All Incidents or Breaches shall have a risk and scope analysis completed by the Information Security Team or their designee. This analysis shall be documented and shared with the Information Security Team, the affected parties, and any other relevant stakeholders. At a minimum, the Information Security Team shall:
| B | Risk Assessment | Identify and assess ongoing risks that may be associated with the Incident or Breach. |
| 1 | Determine the type and breadth of the Incident or Breach | Classify Incident or Breach type, data compromised, and extent of breach |
| 2 | Review data sensitivity | Determine the confidentiality, scope and extent of the Incident or Breach. |
| 3 | Understand the current status of the compromised data | If data has been stolen, could it be used for purposes that harm the individuals whose identity has been compromised; If identity theft is involved, this poses a different type and level of risk. |
| 4 | Document risk limiting processes or technology components that contain and manage the Incident | Does encryption of data/device help to limit risk of exposure? |
| 5 | Determine what technologies or processes will mitigate the loss and restore service | Are there backups of the compromised data? Can they be restored to a ready state? |
| 6 | Identify and document the scope, number of users affected, and depth of Incident or Breach | How many individuals’ personally identifiable information were affected? |
| 7 | Define individuals and roles whose data was compromised | Identify all students, staff, districts, customers or vendors involved in the Incident or Breach |
| 8 | If exploited, what will the compromised data tell a third party about the individual? Could it be misused? | Confidential Information or PII could mean very little to an opportunistic laptop thief while the loss of apparently trivial snippets of information could help a criminal build up a detailed picture associated with identity theft or fraud. |
| 9 | Determine actual or potential harm that could come to any individuals | Identify risks to individuals: Physical Safety Emotional Wellbeing Personal or Business Reputation Financial Implications Identity Concerns A combination of these and other private aspects of their life? |
| 10 | Are there wider consequences to consider? | Is there risk to another LEP, the state, or loss of public confidence? |
| 11 | Are there others who might provide support or advice on risks/courses of action? | Contact all local education providers, agencies, or companies impacted by the breached data, notify them about the Incident, and ask for assistance in limiting the scope of the Incident. |
Notification and Incident Communications
Each security Incident or Breach determined to be ‘moderately critical’ or ‘critical’ shall have communication plans documented by the Management Senior Leadership, and their designees to appropriately manage the Incident and communicate progress on its resolution to all effected stakeholders. At a minimum, the Information Security Team shall:
| C | Notification and Communications | Notification enables affected stakeholders to take precautionary steps and allow regulatory bodies to act on the Incident or Breach. |
| 1 | Are there legal, contractual or regulatory notification requirements associated with the Incident or Breach? | Review vendor contracts and compliance terms, assure state and federal reporting and notifications are understood. Contact HR manager as necessary to begin contractual adherence. Should the Breach include Student PII, initiate the ICE Group Board hearing process. |
| 2 | Notify impacted individuals of Incident or Breach remedies. | Provide individuals involved in the Incident or Breach with mitigation strategies to re-secure data (e.g. change user id and/or passwords etc.) |
| 3 | Determine Internal Communication Plans | Work with senior leadership and provide regular internal updates on status of Incident or Breach, remedies underway, and current exposure and containment strategies. This messaging should be provided to all internal state stakeholders and management. Messaging shall be coordinated through the ICT Department office. |
| 4 | Determine Public Messaging | Prepare and execute a communication and follow-up plan with Information Security Team and senior leadership. Communication strategies need to define audience(s), frequency, messaging, and content. |
| 5 | Execute Messaging Plan | Prepare and execute a communication and follow-up plan with Information Security Team and senior leadership. Communication strategies need to define audience(s), frequency, messaging, and content. |
Post-mortem Evaluation and Response
Each Incident or Breach determined to be “moderately critical” or “critical” shall have a post-mortem analysis completed by the Information Security Team and their designees to appropriately document, analyse, and make recommendations on ways to limit risk and exposure in the future. At a minimum, the Information Security Team shall:
| D | Evaluation and Response | To evaluate the effectiveness of ICE Groups response to the Incident or Breach. |
| 1 | Establish where any present or future risks lie | Assess and evaluate the root causes of the Incident or Breach and any ways to mitigate and/or prevent a similar occurrence. |
| 2 | Consider the data and security measures employed | Assess and evaluate the root causes of the Incident or Breach and any ways to mitigate and/or prevent a similar occurrence. |
| 3 | Evaluate and identify areas of weakness in existing security measures and procedures | Document lapses in process, procedure, or policy that may have caused the Incident or Breach. Analyse and document solutions and remedies to reduce future risks. |
| 4 | Evaluate and identify areas of weakness related to employee skills | Assess employee readiness, education, and training. Document and plan for updates in education or procedural changes to eliminate potential for future Incidents. |
| 5 | Report on findings and implement recommendations | Prepare report and presentation to ICE Group for major Incidents or Breaches. |
Incidents or Breaches. An activity log recording the timeline of Incident management shall also be completed. Reporting and documentation shall be filed and managed through the office of the Information Security Team. Each of these four elements shall be conducted as appropriate for all qualifying
Audit Controls and Management
On-demand documented procedures and evidence of practice should be in place for this operational policy. Appropriate audit controls and management practice examples are as follows:
- Archival completed Incident Reports demonstrating compliance with reporting, communication and follow-through
- Executed communication plans for Incident management
- Evidence of cross-departmental communication throughout the analysis, response and post-mortem processes
Policy Compliance
Compliance Measurement
The ICT Dept. and/or Management will verify compliance to this policy through various methods, including but not limited to, periodic walk-throughs, video monitoring, business tool reports, internal and external audits, and feedback to the policy owner.
Exceptions
Any exception to the policy must be approved by the ICT Dept. and/or Management in advance.
Non-Compliance
An employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment.
Failing to notify a breach when required to do so can result in a significant fine up to 10 million euros or 2 per cent of your global turnover. The fine can be combined the DPC’s other corrective powers under Article 58. It is vital to follow the breach reporting policy and procedure in place to ensure ICE Group detect and can notify a breach, on time; and provide the necessary details to all relevant parties.
Stay Up To Date
Join Our Mailing List Today - Get The Latest Industry Insights & First Look At The Newest Upcoming Training Courses.
GET IN TOUCH
Our Training Team are on hand to assist you with course enquiries, bookings, or scheduling development opportunities.
CALL US
EMAIL US
VISIT US
Galway Business Park, Dangan,
Galway, Ireland.